Phishing Detection & Mitigation Service – Cyber Trasers
Introduction
Phishing remains one of the most widespread and persistent cyber threats in the digital environment. These attacks rely on deception rather than technical exploits, targeting users through emails, messages, websites, or calls that appear legitimate but are designed to extract sensitive information. When successful, phishing can lead to account compromise, financial loss, identity misuse, and long-term security exposure.
At Cyber Trasers, our Phishing Detection & Mitigation service focuses on helping individuals and organizations identify phishing risks, respond effectively to incidents, and strengthen their defenses against future attacks. Our approach emphasizes awareness, secure access practices, and structured response guidance rather than unrealistic guarantees.
Understanding Phishing
What Is Phishing?
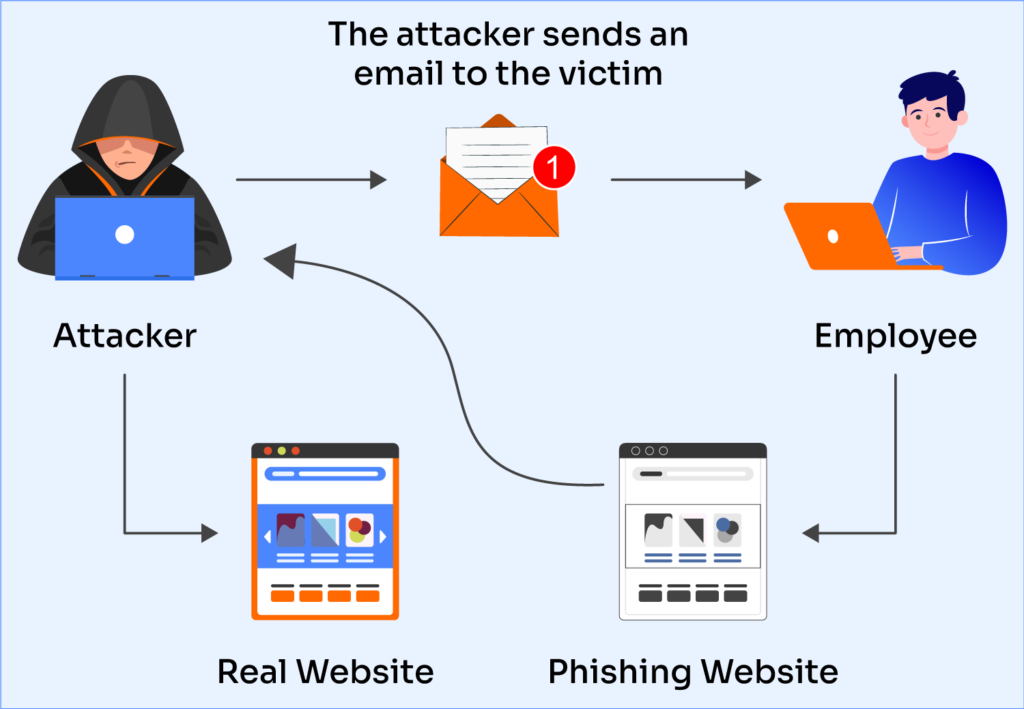
Phishing is a form of social engineering attack in which malicious actors impersonate trusted entities to trick victims into revealing confidential information such as login credentials, recovery phrases, or payment details. These attacks commonly occur through email but may also be delivered via text messages, phone calls, messaging platforms, or social media.
Phishing messages often include misleading links or attachments that redirect users to fraudulent websites or install malicious software.
Common Types of Phishing Attacks
Phishing techniques vary in sophistication and targeting. Common forms include:
Email Phishing
Broad, mass-distributed messages designed to look legitimate and prompt recipients to click links or submit credentials.Spear Phishing
Targeted phishing attempts that use personal or organizational details to increase credibility.Whaling
Highly targeted phishing directed at executives or decision-makers to induce financial transfers or disclosure of sensitive data.Smishing
Phishing delivered via SMS or messaging applications, often impersonating banks or service providers.Vishing
Voice-based phishing conducted through phone calls that pressure victims into revealing information or authorizing actions.Clone Phishing
Legitimate emails are copied and modified with malicious links or attachments, making them harder to identify.
How to Reduce the Risk of Phishing Attacks
While phishing cannot be eliminated entirely, the following practices significantly reduce risk:
Be Cautious with Unsolicited Messages
Treat unexpected requests for information or action with skepticism.Verify Links and Senders Carefully
Inspect URLs and sender details before clicking or responding.Use Multi-Factor Authentication (MFA)
MFA adds protection even if credentials are compromised.Keep Systems and Applications Updated
Updates often address known vulnerabilities.Improve Awareness and Training
Understanding phishing tactics improves detection and response.Confirm Sensitive Requests Independently
Verify requests through official channels rather than message links.
How Cyber Trasers Assists With Phishing Detection & Mitigation
Our Phishing Detection & Mitigation service follows a structured, prevention-focused approach.
Step 1: Initial Consultation & Risk Review
We begin with a confidential discussion to understand your exposure, account usage, and any recent incidents.
Step 2: Threat & Access Assessment
We review affected accounts, access points, and authentication practices to identify potential weaknesses.
Step 3: Incident Response Guidance
If phishing has already occurred, we assist with stabilizing compromised access, resetting credentials, and limiting further exposure.
Step 4: Monitoring & Mitigation Support
We provide guidance on monitoring suspicious activity and responding quickly to emerging threats.
Step 5: Prevention & Best-Practice Recommendations
Clients receive tailored recommendations to strengthen security habits, improve account configuration, and reduce future risk.
Recognizing Phishing & Related Scam Indicators
Common warning signs include:
Urgent or threatening language
Requests for confidential information
Unexpected links or attachments
Generic greetings or formatting inconsistencies
Slight variations in sender addresses or domains
Early recognition often prevents escalation.
About Our Phishing Detection & Mitigation Service
Cyber Trasers Phishing Detection & Mitigation service is designed to help clients reduce exposure, respond effectively to incidents, and improve long-term digital security. Our guidance is based on technical understanding, realistic assessment, and clear communication rather than fear-based messaging or exaggerated claims.
All cases are handled confidentially, with a strong emphasis on prevention and education.
Why Choose Cyber Trasers?
Cybersecurity & Digital Asset Expertise
Experience assessing phishing incidents and access compromise scenarios.Confidential & Secure Handling
Sensitive information is managed using strict privacy-focused protocols.Prevention-First Approach
Emphasis on stopping phishing before damage occurs.Transparent Guidance
Honest assessments with realistic expectations.Long-Term Security Focus
Support extends beyond immediate incidents to improved digital safety.